Introduction In the realm of wireless communication, both LTE (Long-Term Evolution) and 5G networks play pivotal roles in providing high-speed connectivity. However, when it comes to security, there are notable differences between the two generations. Let’s explore the comparison of LTE vs. 5G security features. LTE vs. 5G security comparison table Sr. No. Security Feature… Continue reading LTE vs. 5G security: A Comparison of Security Features
Author: user
Enhancing 5G Security: A Comprehensive Approach
Introduction We need to understand the paramount importance of robust 5G security measures in the era of 5G connectivity. As businesses and individuals embrace the potential of this transformative technology, it is crucial to address the inherent security considerations to protect sensitive data, ensure privacy, and safeguard against emerging threats. In this article, we delve… Continue reading Enhancing 5G Security: A Comprehensive Approach
Protecting Your Network from DNS Tunneling: Effective Solutions
Introduction As the threat of DNS tunneling looms over organizations, it becomes imperative to implement robust measures to safeguard network infrastructure from this stealthy technique. By adopting a multi-layered approach and leveraging advanced security solutions, you can fortify your network defenses and mitigate the risks associated with DNS tunneling. In this article, we explore some… Continue reading Protecting Your Network from DNS Tunneling: Effective Solutions
DNS Tunneling: Unveiling the Hidden Potential
Introduction In the vast landscape of cyber security, one concept that has been gaining attention is DNS tunneling. This innovative technique allows the transmission of unauthorized data through DNS queries and responses, bypassing traditional security measures. DNS tunneling has sparked discussions and concerns among experts, as it presents both opportunities and risks. In this article,… Continue reading DNS Tunneling: Unveiling the Hidden Potential
Enhancing User Protection in a Hyper connected World: Leveraging DNS
Introduction Welcome to our comprehensive guide on leveraging DNS (Domain Name System) to protect users in an increasingly hyper connected world. we need to understand the critical importance of safeguarding user data and privacy in today’s digital landscape. In this article, we will explore the role of DNS in enhancing user protection, mitigating potential threats,… Continue reading Enhancing User Protection in a Hyper connected World: Leveraging DNS
10 Innovation Areas in 5G: Advancements and Beyond
Introduction Welcome to our comprehensive guide on the innovation areas within the realm of 5G technology. Many companies are working and developing cutting-edge solutions that push the boundaries of what’s possible with 5G and pave the way for a future of enhanced connectivity. In this article, we will delve into ten key innovation areas that… Continue reading 10 Innovation Areas in 5G: Advancements and Beyond
Exploring the Benefits and Features of Secure Access Service on Edge (SASE) Architecture
SASE Architecture Benefits. With the increasing number of cyber threats and the rise of remote work, there is a growing need for a security solution that can provide comprehensive protection for distributed networks. Secure Access Service on Edge (SASE) is a new architecture that combines networking and security into a single cloud-based solution. This article… Continue reading Exploring the Benefits and Features of Secure Access Service on Edge (SASE) Architecture
Understanding Link Aggregation Control Protocol (LACP) for Enhanced Network Performance
Introduction Link Aggregation Control Protocol (LACP) plays a vital role in optimizing network performance by combining multiple physical network links into a single logical link. This protocol helps businesses achieve increased bandwidth, improved fault tolerance, and load balancing capabilities. In this article, we will delve into the fundamentals of LACP, explore its benefits, and discuss… Continue reading Understanding Link Aggregation Control Protocol (LACP) for Enhanced Network Performance
Radio Access Network in 5G
Radio access network in 5G Radio access network (RAN) hardware consists of antennas, radio units, and baseband units. RAN software includes network functions which is responsible for data transmission, QoS (quality of service), signal handover, and management and orchestration. RAN Hardware The RAN node hardware consists of the antennas, radio units, and baseband units. Antenna… Continue reading Radio Access Network in 5G
What is Disaggregation?
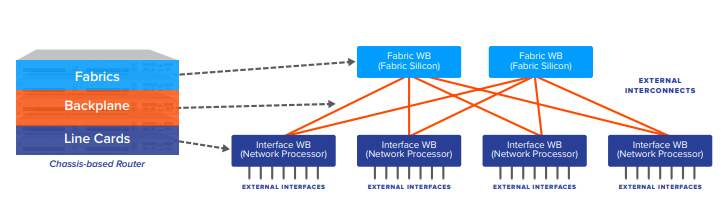
What is Disaggregation? We have heard disaggregation in the server side a lot. Server virtualization is famous from quite a long time. Hypervisor is mainly used to disaggregate from physical server to operating system. Cloud native implementation is enable even operating system disaggregation. There are so many network evolution and architectural changes are being talked… Continue reading What is Disaggregation?