Introduction The internet is an ever-changing space, and so are the associated threats and vulnerabilities. One such threat is BGP hijacking, which is on the rise and has the potential to cause significant damage to organizations that rely on the internet. In this article, we will explore BGP hijacking, how it works, its dangers, and… Continue reading The Dark Side of BGP Hijacking: What You Need to Know to Protect Your Network
Category: Network Protocol
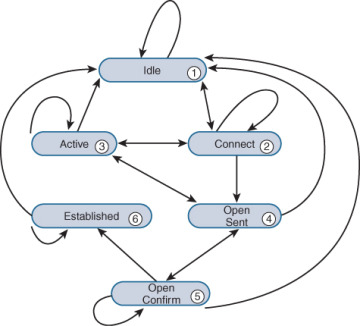
BGP States: Understanding the Journey of Routing Information
Introduction In the realm of networking and internet communication, the Border Gateway Protocol (BGP) plays a pivotal role in facilitating the exchange of routing information between autonomous systems. BGP operates through a series of states that govern the establishment, maintenance, and termination of connections between routers. In this article, we will explore the different BGP… Continue reading BGP States: Understanding the Journey of Routing Information
Border Gateway Protocol (BGP): The Backbone of Internet Routing
Introduction In today’s interconnected world, where the internet plays a vital role in connecting people and organizations across the globe, it is crucial to have robust routing protocols that enable efficient data transmission. One such protocol that serves as the backbone of internet routing is the Border Gateway Protocol (BGP). In this comprehensive guide, we… Continue reading Border Gateway Protocol (BGP): The Backbone of Internet Routing