Introduction to the NTP Protocol In today’s interconnected world, accurate timekeeping is crucial for various computer systems, networks, and applications. From financial transactions to data synchronization, maintaining precise time across devices is essential. The Network Time Protocol (NTP) was developed to address this need and ensure synchronized clocks throughout networks. The Importance of Time Synchronization… Continue reading Understanding the NTP Protocol
BGPsec: Enhancing Security in Border Gateway Protocol
Introduction In today’s interconnected world, where data communication plays a pivotal role, ensuring the security of internet routing protocols is of utmost importance. The Border Gateway Protocol (BGP) is a vital protocol that allows autonomous systems (ASes) to exchange routing information. However, BGP has been susceptible to various security vulnerabilities, compromising the stability and security… Continue reading BGPsec: Enhancing Security in Border Gateway Protocol
Benefits of RPKI over other BGP security solutions
Introduction There are several benefits of RPKI over other BGP security solutions. The RPKI benefits are described below. It’s important to note that while RPKI offers significant benefits, it is not a standalone solution for all BGP security challenges. It is often used in conjunction with other security mechanisms, such as BGPsec, to provide comprehensive… Continue reading Benefits of RPKI over other BGP security solutions
RPKI solutions for BGP route hijacking
Introduction RPKI (Resource Public Key Infrastructure) provides effective solutions for mitigating BGP (BorderGateway Protocol) route hijacking. RPKI solutions Here are the key RPKI solutions for addressing this issue: Route Origin Validation: RPKI enables the validation of the origin of BGP routes. Network operators can digitally sign their IP address prefixes and Autonomous System (AS) numbers… Continue reading RPKI solutions for BGP route hijacking
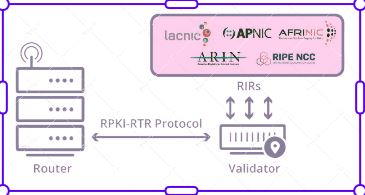
RPKI: Resource Public Key Infrastructure
Introduction Resource Public Key Infrastructure (RPKI) is a security framework designed to enhance the reliability and security of the Border Gateway Protocol (BGP) routing system, which is fundamental to the functioning of the Internet. RPKI provides a mechanism for verifying the authenticity and validity of Internet Protocol (IP) address prefixes and Autonomous System (AS) numbers,… Continue reading RPKI: Resource Public Key Infrastructure
The Dark Side of BGP Hijacking: What You Need to Know to Protect Your Network
Introduction The internet is an ever-changing space, and so are the associated threats and vulnerabilities. One such threat is BGP hijacking, which is on the rise and has the potential to cause significant damage to organizations that rely on the internet. In this article, we will explore BGP hijacking, how it works, its dangers, and… Continue reading The Dark Side of BGP Hijacking: What You Need to Know to Protect Your Network
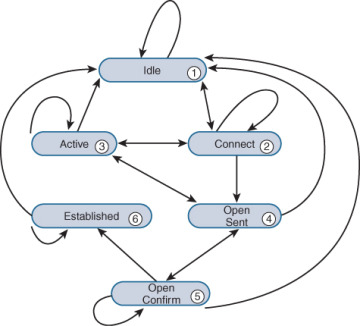
BGP States: Understanding the Journey of Routing Information
Introduction In the realm of networking and internet communication, the Border Gateway Protocol (BGP) plays a pivotal role in facilitating the exchange of routing information between autonomous systems. BGP operates through a series of states that govern the establishment, maintenance, and termination of connections between routers. In this article, we will explore the different BGP… Continue reading BGP States: Understanding the Journey of Routing Information
Border Gateway Protocol (BGP): The Backbone of Internet Routing
Introduction In today’s interconnected world, where the internet plays a vital role in connecting people and organizations across the globe, it is crucial to have robust routing protocols that enable efficient data transmission. One such protocol that serves as the backbone of internet routing is the Border Gateway Protocol (BGP). In this comprehensive guide, we… Continue reading Border Gateway Protocol (BGP): The Backbone of Internet Routing
Quantum Computing: Unleashing the Power of the Future
Introduction Quantum computing is an emerging field that holds immense promise in revolutionizing the way we process information and solve complex problems. With the exponential growth of data in today’s digital age, traditional computing methods are reaching their limits. Quantum computing offers a new paradigm, harnessing the principles of quantum mechanics to perform computations at… Continue reading Quantum Computing: Unleashing the Power of the Future