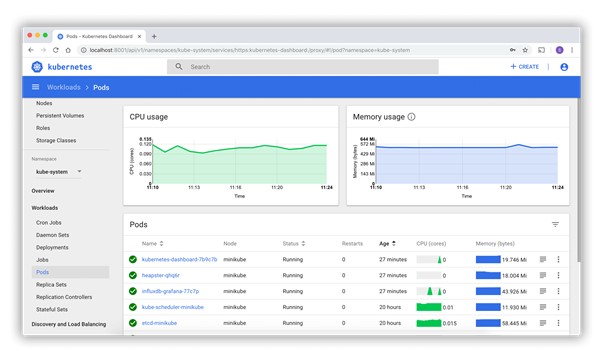
Kubernetes Dashboard The Kubernetes Dashboard provides a web-based user interface for Kubernetes cluster management. Minikube installs the Dashboard as an addon, but it is disabled by default. Prior to using the Dashboard we are required to enable the Dashboard addon, together with the metrics-server addon, a helper addon designed to collect usage metrics from the… Continue reading Kubernetes Dashboard
Install Kubectl
Kubectl kubectl allows us to manage local Kubernetes clusters like the Minikube cluster, or remote clusters deployed in the cloud. It is generally installed before installing and starting Minikube, but it can also be installed after the cluster bootstrapping step. A Minikube installation has its own kubectl CLI installed and ready to use. However, it… Continue reading Install Kubectl
Docker Installation On Ubuntu
Docker Installation On Ubuntu Step By Step First uninstall old versions if any adminuser@mysystem:~$ sudo apt-get remove docker docker-engine docker.io containerd runc Reading package lists… Done Building dependency tree Reading state information… Done E: Unable to locate package docker-engine adminuser@mysystem:~$ sudo apt-get update Hit:1 http://in.archive.ubuntu.com/ubuntu focal InRelease Hit:2 http://in.archive.ubuntu.com/ubuntu focal-updates InRelease Hit:3 http://in.archive.ubuntu.com/ubuntu focal-backports InRelease… Continue reading Docker Installation On Ubuntu
Installing Minikube on macOS
Installing Minikube on macOS Let’s learn how to install the latest Minikube release on macOS with VirtualBox v6.1 specifically. NOTE: For other VirtualBox and Minikube versions the installation steps may vary! Check the Minikube installation! Verify the virtualization support on your macOS in a terminal (VMX in the output indicates enabled virtualization): $ sysctl -a… Continue reading Installing Minikube on macOS
Minikube Installation
Minikube Installation on Linux system Let’s find out how to put in the most recent Minikube release on Ubuntu linux system 20.04 LTS with VirtualBox v6.1 specifically. NOTE: For different Linux system OS distributions or releases, VirtualBox and Minikube versions, the installation steps could vary! Check the Minikube installation! Verify the virtualization support on your… Continue reading Minikube Installation
What is multi access edge computing?
What is multi access edge computing? Multi-Access Edge Computing (MEC) in 5G moves the processing of traffic and services from a unified cloud located at central location to the edge of the network and nearer to the client. Rather than sending all information to a cloud for handling, the data’s are processed, analyzed and stored… Continue reading What is multi access edge computing?
Intend based analytics (IBA)
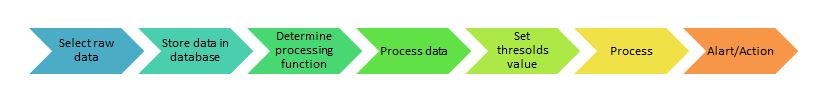
Intend based analytics A proper IBN system uses intent-based analytics (IBA) to stay aware of network changes in real time, continually ensuring that your services remain in compliance with your intent. That’s intent assurance. Change management: IBN system shall provide change management. There are two types of changes normally we observed in the network. Uncontrolled… Continue reading Intend based analytics (IBA)
Intend Based Networking Close Loop Automation life cycle
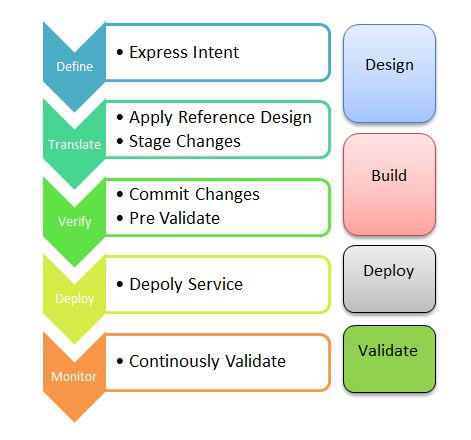
Intend Based Networking Close Loop Automation life cycle An intend based automation life cycle is depicted as below. IBN workflows defined as below: Define the intent. Translate intent into a series of prescriptive network changes. Verify that the changes are valid before deploying them. Deploy the verified changes. Monitor network state to ensure continuous compliance… Continue reading Intend Based Networking Close Loop Automation life cycle
Intend based networking
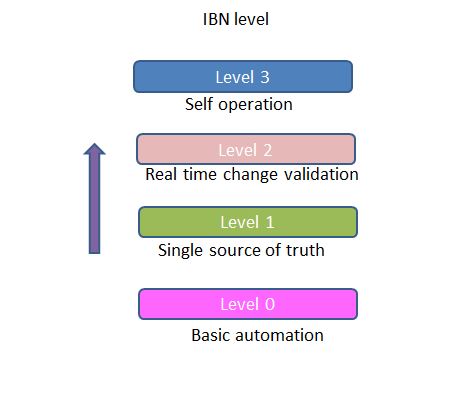
What is intend Based Networking (IBN)? Intend based networking is networking software that is used to manage end to end network life cycle. End to end network life cycle management includes plan, design and implement/operate. In layman term, we can say we are putting our network in the auto pilot mode with the help of… Continue reading Intend based networking
network slicing in 5g
What is network slicing in 5G? 5G network slicing is nothing but logically dividing a physical network into multiple virtual networks. Each virtual network will cover specific use case requirements. Here network slice will isolated from each other in control and user plan. Each user will be experienced dedicated services as like they are using… Continue reading network slicing in 5g