Standard Approach To deploy MACsec (802.1AE) over MPLS L3VPN with Post-Quantum Cryptography (PQC), follow this structured approach: 1. Use PQC-Ready MACsec Key Agreement (MKA) 2. Integrate a PQC Key Server 3. Key Exchange Call Flow with PQC Server Here’s how MACsec key exchange works with PQC: 4. Deployment Models Scenario Implementation PQC Requirement PE-CE Encryption MACsec on customer… Continue reading Implementing MACsec over MPLS L3VPN with Post-Quantum Cryptography (PQC)
Author: user
Implementing MACsec over MPLS L3VPN: Best Practices and Standard Approach
MPLS L3VPNs provide scalable, multi-tenant connectivity, but they lack native encryption. While IPsec is commonly used, MACsec (802.1AE) offers a high-performance alternative for securing MPLS L3VPN traffic at line rate (1G–100G+) without IPsec’s bottlenecks. Here’s the standard approach to deploying MACsec over MPLS L3VPN: 1. Understand Where MACsec Fits in MPLS L3VPN MPLS L3VPN operates at Layer 3, while MACsec works at Layer 2 (Ethernet). This… Continue reading Implementing MACsec over MPLS L3VPN: Best Practices and Standard Approach
MACsec: The Future of High Speed Ethernet Encryption for WAN Security
Introduction: The Need for Faster, More Secure Networks The explosion of cloud computing, IoT, and video streaming has pushed WAN bandwidth demands to unprecedented levels. While Ethernet speeds have evolved from 10G to 100G and beyond, encryption technologies have struggled to keep up. Enter MACsec (802.1AE)—a Layer 2 encryption standard that provides line-rate security without compromising performance. Unlike traditional IPsec, which operates at the IP… Continue reading MACsec: The Future of High Speed Ethernet Encryption for WAN Security
The Future of Telecom: AIOps and AI-Driven Network Management
A New Approach to Network Management: The Role of AIOps in Digital Transformation The complexity of managing modern telecom networks continues to grow, driven by increasing data demands, expanding endpoints, and evolving network architectures. Service providers are grappling with the need to maintain efficiency while scaling operations and offering cutting-edge services. In this evolving landscape,… Continue reading The Future of Telecom: AIOps and AI-Driven Network Management
Unveiling the Future of AI: The Crucial Role of Networking in Training and Inference
Artificial Intelligence (AI) has rapidly evolved from a futuristic concept to a cornerstone of modern technology. From natural language processing and computer vision to autonomous vehicles and virtual assistants, AI is reshaping industries and transforming the way we interact with technology. As we continue to push the boundaries of what AI can achieve, it’s clear… Continue reading Unveiling the Future of AI: The Crucial Role of Networking in Training and Inference
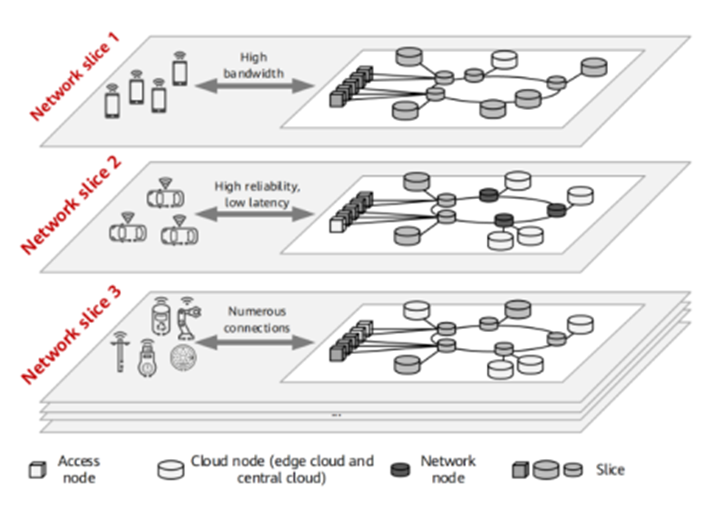
Revolutionizing Network Services with SRv6-Based Network Slicing in the 5G Era
Introduction In this article, we are going to discuss about need for network slicing in 5G era and how SRv6 can help us to achieve network slicing to fulfil the requirement of 5G. In the fast-evolving landscape of telecommunications, the traditional design of IP backbone, metro, and mobile bearer networks has posed challenges for seamless… Continue reading Revolutionizing Network Services with SRv6-Based Network Slicing in the 5G Era
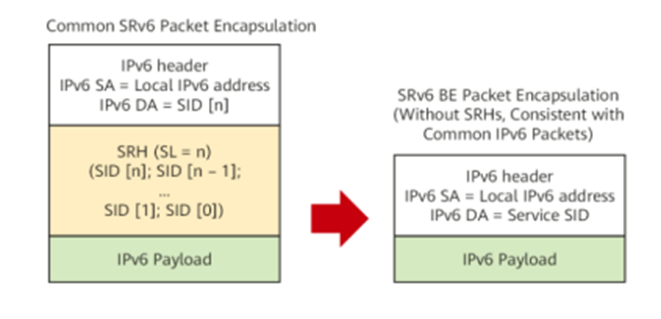
Demystifying SRv6 BE: Streamlining MPLS in IP Networks
Understanding SRv6 BE in Networking Traditional MPLS (Multiprotocol Label Switching) relies on control plane protocols like LDP (Label Distribution Protocol) and RSVP-TE. SRv6 BE (Segment Routing over IPv6 Best Effort) simplifies this by utilizing only one service SID (Segment Identifier) for guiding packet forwarding in best-effort mode on an IP network. Unlike traditional MPLS, SRv6… Continue reading Demystifying SRv6 BE: Streamlining MPLS in IP Networks
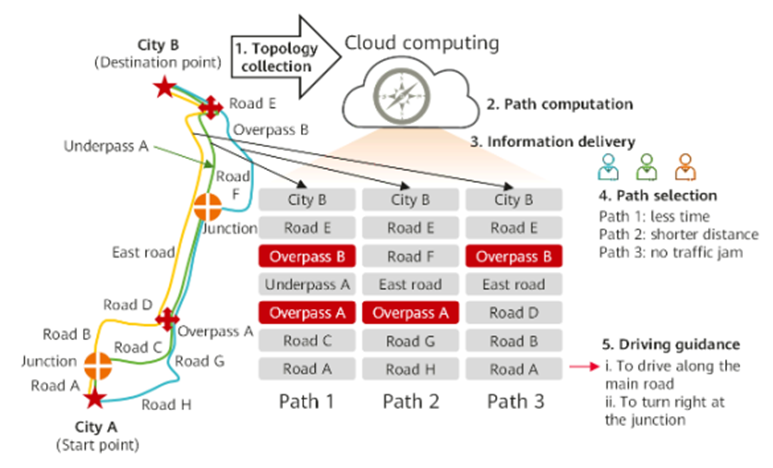
Optimizing Network Traffic with SRV6 TE Policy: A Comprehensive Guide
What Is SRV6 TE Policy? SRV6 TE Policy utilizes the source routing mechanism of SR to direct packet forwarding based on a predefined list of segments encapsulated by the headend. The concept of SRv6 TE Policy can be likened to navigating through a map, as illustrated in Figure below, to elaborate on SRv6 TE Policy.… Continue reading Optimizing Network Traffic with SRV6 TE Policy: A Comprehensive Guide
Unveiling SRv6’s Elegance: Ensuring Faultless Reliability in IP Bearer Networks
Introduction Imagine a world where important services like government, finance, and healthcare rely on super-strong networks. These networks need to be available almost all the time—99.99% to be exact. And when it comes to the latest 5G services, like the ones for super-fast and reliable communication, they demand even more—99.999% availability. Think of it like… Continue reading Unveiling SRv6’s Elegance: Ensuring Faultless Reliability in IP Bearer Networks
Revolutionizing Network Programmability: Navigating the Three-Dimensional Realm with SRv6 Mastery
Introduction The intricacies embedded in SRv6 breathe new life into the importance of SIDs, extending their role beyond mere representations of paths and various service types. SRv6 SIDs, at their core, act as catalysts, amplifying the flexibility and intelligence of network programmability. A crucial aspect of this advancement lies in the collaborative support from IGP… Continue reading Revolutionizing Network Programmability: Navigating the Three-Dimensional Realm with SRv6 Mastery